7-8 Grade Safe Connects
Slide 1

What is Net Literacy? We are a nonprofit “youth empowered” organization that benefits from the experience of adult mentoring. The Net Literacy Corporation has five digital inclusion programs, and this evening we will focus on our Safe Connects program.
Okay, this is what we’re going to do today. First – for teens and parents – we’re going to talk about what’s happening on the Internet because knowledge and education means that you’ll have a safer and all around better online experience. Next, we’ll get into the details with a presentation by the Safe Connects Team.
Are you ready for this? Here’s some very interesting information for parents and students!
For parents – 45% of all 5th graders in an I-Safe study said that if their parents knew everywhere they went online, they would either take their computer away, express concern, or restrict my internet usage.
For teens – if anything or anyone ever bothers or concerns you while you’re online, just shut your computer down and talk to your parents or another trusted adult.
For teens and parents – 83% of the people online have admitted to lying to others while being online.
For parents – we recommend you have a family discussion about placing your children’s and family computer in an open area – not in anyone’s room
For teens – your parents should respect your privacy even though you realize that they are responsible for your safety.
For parents – 42% of all kids have been cyber bullied online and 35% have been threatened online.
For teens – never agree to meet a stranger that you’ve meet online and have previously met in person. If you have questions about this – ask your parents. And parents – 12% of all students have said they’ve meet a stranger they met online “face to face.”
For parents and teens – in an I-Safe study, 87% of all adults said that they had made specific rules for their children’s Internet use – while only 36% of the students said their parents had – this is a gap of 51% of what parents think and students think!
For parents and teens – in the same study, 69% of the parents said they know a lot about what their children do on the Internet – while 41% of the students say they don’t share what they do online with their parents. That’s a 28% gap, let alone the 31% of parents that say they don’t know a lot about what their children do online!
For everyone – you can find more information by going to safeconnects.org.
Slide 2

Today you’ll learn how to stay safe while using the Internet. We’ll discuss topics including passwords, net predators, profiles, netiquette, e-mail, viruses, chat rooms, and community websites.
Slide 3

First we will start today’s program by discussing passwords.
Slide 4

Many of us has heard of the term, “password, but what does it really mean?
Password is a secret combination of letters and numbers used to access different programs, such as email, games, and websites.
Slide 5

There are a few simple things to remember when choosing a secret password:
1) Passwords should be something you can remember, don’t create overly complicated passwords unless you are confident you can remember them.
2) Don’t create passwords that are easy to guess – too many people use their dog’s name or their middle name for a password. These are too easy for others to guess.
3) If you use the same password on each website – knowing one password can give someone access to all of your sites.
4) If you write your password down, make you put in in a safe and secure location.
Slide 6

Okay, now that you know about passwords – I want you to tell me if these are good or bad passwords for a student neamed Andrew Smith. Let’s go through this together.
Secret1 – Okay is Secret1 a good password…it’s not so good because it’s easy to guess.
Mypassword – What about Mypassword…it’s not so good because it’s also easy to guess.
Asmith – How about Asmith? Bad…because it’s just Andrew’s first initial and his last name – too easy to guess.
F3d20w9 – What about F3d20w9. Whew! It’s good – if you can remember it – no one would ever guess it.
Andrew – And what would you say about Andrew? If you said it’s too easy to guess and a bad password – you’d be right.
Password1234 – Okay, for Password1234, you’re right if you said it was too easy to guess.
Freethepanda – Freethepanda – that’s just a made up word – so that’s a good one – tough to guess.
Smith – Okay, what about Smith? For everyone that said “too easy,” you’d be right!
Pokadots – Pokadots – is a good password – if it’s a word that you just decided to use and doesn’t have any special meaning.
Safeconnectsrox – And lastly, Safeconnectsrox – it’s a good name because it’s true but more importantly, no one would ever guess it.
Slide 7

Next, let’s discuss chat rooms, private chat rooms, and instant messaging – sometimes called “IMing.”
Slide 8
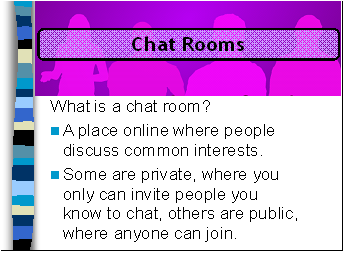
A chat room is a place or location online where people can discuss a common interest. Just like any other place, the Internet has good and bad people, so you have to be careful. Some chat rooms are “private” where you or another person in the chat room must “invite” another person to join, while others are open for anyone to join. First, never allow yourself to be invited into a private chat room unless it’s with a friend that goes to your school or you know well. Public chat rooms can also create problems.
Slide 9

If you are in any chat room and you see people you don’t know or don’t like the tone of the conversation, consider leaving it. It’s as simple as that. When you’re in a chat room, you don’t know if you are talking to a friend’s friend or a complete stranger. Strangers on the Internet and chat rooms can be dangerous, and it’s just not worth getting involved.
Slide 10
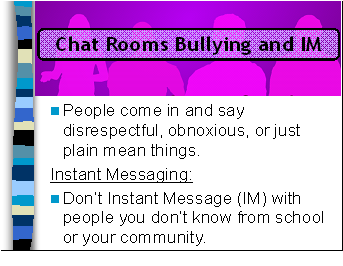
Some people go into chat rooms just to cause trouble and be mean. This is called “chat room bullying.” Comments can be made about your race, religion, if you’re a girl, a boy, or for no reason at all. They probably don’t even know who you are – some people get their kicks by trying to hurt others.
Instant messaging is a one-to-one voice or text conversation that is available via the Internet. If someone tries to Instant Message you and you don’t know them – don’t answer them just like you wouldn’t have discussions with strangers that you don’t know in real life. And remember, you can’t see or hear this stranger – so don’t IM unless it’s with a friend that you already know.
If worst comes to worst, and you feel uncomfortable or threatened, just turn your computer off and talk to your parents. Moreover, if someone who talks to you online asks to meet you in public, don’t meet them, and most importantly, tell a parent or a trusted adult.
Slide 11

Now we’re going to talk about profiles.
Slide 12

A profile is a page where you tell others about yourself and is usually used in chat rooms, web communities and personal websites.
Slide 13

Some people write profiles and others choose not to. Talk to your parents if you are thinking about writing a profile, and see what they say. Sometimes writing a profile can put you at risk. If your parents agree that it’s OK, we recommend that in your profile, you talk about your favorite hobbies, TV shows and games, but NOT about your personal information. Don’t include your full name, family information, and absolutely don’t include your address and phone number.
Slide 14

Now, let’s discuss Net predators.
Slide 15

What is a Net predator? A Net predator is an adult who used the Internet with the intention of harming teens. The Internet is just like the real world – both good and bad people are online. And some people are just evil, such as Internet predators.
Net predators often go into chat rooms pretending to be teens in order to gain their trust. Remember, the internet is a pretty anonymous place. Anyone can pretend to be anything. And sometimes Net predators will spend months working to gain a teens trust.
Slide 16

Eventually, they will invite you to meet them in a face-to-face meeting. They want to meet you to hurt you or force you to do something that you don’t want to do. If anyone that you don’t know in real life asks you to meet them face-to-face – immediately tell a parent or a trusted adult.
Never agree to a face-to-face meeting with someone that you’ve met over the Internet.
Slide 17

There are a few simple things you can do to avoid becoming a victim of an Internet predator: Use common sense and make reasonable choices. Avoid sharing personal information such as full name, address and telephone, and don’t post a picture of yourself. If you ever feel unsafe, or know that someone online is doing something wrong, again, talk to your parents or a trusted adult.
Slide 18

Our next topics is Internet etiquette…or Netiquette. Netiquette is using appropriate language and treating others as you’d like to be treated on the Internet.
Slide 19

Having a conversation online is just like having a conversation in person or on the phone. Just because the person can’t see you, doesn’t mean that you can act differently; it’s still important to be polite.
Here are the rules of the Internet for using good Netiquette:
– First, only type things that you would say to a person if you were in the same room with them.
– Second, don’t swear or make offensive comments because someone’s feelings may be hurt
– Third, it’s illegal to post false statements about someone
– Fourth, facial expressions are not able to be read on the Internet, so make sure to let a person know when you are joking; do not joke in what someone might misunderstand as offensive
Slide 20

Good Netiquette is easy – just treat others like you’d want to be treated when you’re online.
Slide 21

Our next topic is chain mail – which is junk mail, hoaxes, and people trying to sell you stuff over the Internet.
Slide 22

Have your ever been sent a chain letter?
You probably recognize one when you see it: With subjects ranging from friendship to religion to good luck, you’re supposed to e-mail the letter to a specific number of other
people with directions on how they should “continue the chain.” Usually a chain letter threatens consequences to those who don’t pass the message on.
Slide 23

People used to send chain letters in the mail, but now they send them using e-mail. These letters focus on many different topics – such as hoaxes, rumors, jokes, but the main idea of all chain letters is to pass it on to a certain number of people in order to keep the chain going.
Slide 24

The problem is that when you pass on a chain letter you are also passing out the e-mail addresses of the other people that you sent it to, making it easier for them to get computer viruses. So when it comes to chain mail – break the chain and don’t forward chain mail on to others.
Slide 25

Malware – it’s a destructive way people that some people will use to try to break your computer or cause you to lose all of the information you’ve stored on your computer.
Slide 26

What is malware?
Malicious is computer software that can copy itself to computer without the end user’s knowledge
It can cause serious damage to a computer system, including loss of data, theft of sensitive information (such as credit card numbers), and general system slowdowns.
Malware can replicate and modify itself to infect other computers through a network or storage media such as flash drives and floppy disks.
Slide 27
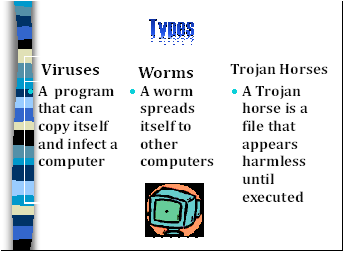
There are several types of malware – including viruses, worms, and Trojan horses.
A computer virus is a computer program that can copy itself and infect a computer without permission or knowledge of the user.
A worm can spread itself to other computers without needing to be transferred as part of a host
A Trojan horse is a file that appears harmless until executed. In contrast to viruses, Trojan horses do not insert their code into other computer files
Slide 28

Your computer can become infected by:
– Instant Messaging – if you instant message with a strange – the stranger can IM you a virus
– Online downloads of music, videos, or programs can have viruses in them and can infect a computer. One way of reducing the chances of receiving a virus from a download file is to never download pirated content.
– Never download an email attachment unless it’s from someone you know and is something that you expect. A friends computer can become infected and send an email with an attachment that contains a virus.
– Clicking on links that lead to harmful sites – did you know that a recent survey by Google indicated that 10% of all of the website on the Internet are infected with some type of malware. Just one click on one of these websites will cause your computer to become infected.
Slide 29

Viruses spread when you open a file attached to email, through Instant Messaging, or by downloading games or programs that have a virus implanted in them.
So how do you prevent a virus from infecting your computer? First, make sure that you have anti-virus software on your computer and keep it up to date so your subscription doesn’t expire. Secondly, use common sense. Be as careful on the Internet as you are when you cross the street – since we know that viruses are out there – use good judgment and don’t open anything from someone you don’t know. Even if a friend that you know sends you an email that seems strange or out of character (such as them sending you an attachment that says “love”) – don’t open it – call them first to check that it was really them that sent it. Third, use antivirus software and a firewall.
Slide 30

What are spyware and adware?
Any software that covertly gathers user information through the user’s Internet connection without his/her knowledge, usually for advertising purposes.
Spyware applications are typically bundled as a hidden component of freeware or shareware programs that can be downloaded from the Internet.
Slide 31
Basically, both types of programs track anyone that uses your computer. Adware shows advertisers how you use the Internet – so they can more effectively try to sell you things by placing advertising on a site that might appeal to your interest or to test advertising. They usually don’t know specifically who you are – but usually gather information from millions of computer users. They do slow down your computer. Spyware is much more serious – once it is on your computer, it can secretly determine your passwords and have other confidential information on your computer sent to the person that created the spyware.
Slide 32

Here are the four ways to get spyware and adware. Let’s say you get an email that asks you to go to a website that you have never heard of before – if you go to that site – even if you don’t click on anything, a spyware or adware can be secretly downloaded into your computer. That’s why having a firewall is so important. Don’t download a program or open an email attachment unless you are certain that you know who it is from and that it is doesn’t contain a virus, worm, Trojan Horse, or other program that could install adware or spyware on your computer. Stick with toolbars from reputable companies that you’ve heard of before – such as Google.com.
Slide 33

We have discussed viruses, spyware, and adware – and now know that antivirus software and a firewall should be installed on every computer. Also, there are free versions of programs like Adaware SE and Spybot that can be downloaded via the Internet – and will help computer users keep spyware and adware from taking over their computer. Adaware SE and Spybot: Search and Destroy can be found on the Internet at www.download.com or by conducting a search on these products. The free versions of anti-spyware and anti-adware software should be run every couple of days – since they do not automatically eliminate spyware and adware as anti-virus software does.
Slide 34

Okay, our next topic is Cyber Bullies.
Slide 35

What are Cyber Bullies?
Cyber Bullying are people that use e-mail, cell phones pager text messages, instant messaging, defamatory blogging, and defamatory online personal polling Web sites to deliberately and repeatedly engage in hostile behavior to an individual or group, that is intended to harm others.”
Slide 36

Cyber bullying is the fastest growing type of bullying
How can you avoid being a target of Cyber Bulling? If you are sent an abusive e-mail, don’t write back. The sender wants you to reply to be able to harass you further, so don’t give them that satisfaction.
If you receive an e-mail sent to you by a cyber bully – use the Take 5 Method. Just put the mouse down, count to 5, and move on to something else. What you don’t do won’t affect you and if you don’t respond…
You can also “Stop, Block, and Tell”
STOP: Don’t do anything. Take 5 and calm down
BLOCK: Stop the cyber bully. Most IM services offer a block feature. Also, only talk to friends
on your Buddy List.
TELL: Tell a parent or trusted adult. They can help provide some valuable advice and maybe
even work out a solution to stop the bully.
Slide 37

What are community websites? They are websites where people go to meet other people, tell others about themselves, and develop a virtual web-community. However, community websites have the potential of providing others too much information about yourself and can create a dangerous environment. Let’s talk more about what web communities are and how they can be dangerous.
Slide 38

Just like in real life, there is good and bad on the Internet. Sometimes, websites that were not created for harm get used for unintended purposes. One group of websites that falls into this category includes community websites. There are many community websites out there including MySpace, Facebook, and BlackPlanet, just to name a few. MySpace is one of the most popular web-community on the planet, having over 100 million members, and Facebook has over 600 member members. Since they’re their two of the most visited website in the world, we’ll talk about them and since both are similar, we’ll focus on MySpace. This is a copy of their home page.
Slide 39
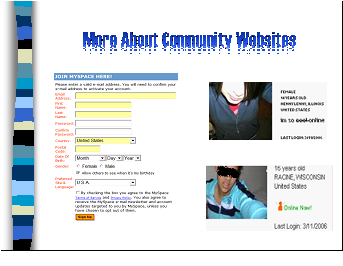
Most of these web-communities target teenagers and individuals in their teens and 20’s. When registering for an account at Myspace, you have to fill out forms with your name, your country, your gender, your e-mail address and your date of birth. If the computer realizes you are 14 or younger, you will be denied an account. But that doesn’t mean that students don’t “pretend” to be 15, 18 or even 21 for that matter. The fact is, many pre-teens lie when they register, so that they can join their “friends” online.
Slide 40
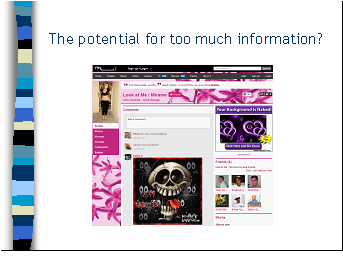
Once you register you fill out a bunch of boxes and fields with interests, occupation, hobbies, a picture etc. The website uses this information to help users find and talk to old friends, and meet new friends. But, of course, this functionality presents risks to the uninformed. If you are in 7th or 8th grade, here’s a good rule to follow before deciding to join a community website – first talk it over with a parent or a trust adult. They can help you decide if it’s right for you. If they say it’s okay, ask them to look at your online profile to make sure that you are safe.
Slide 41
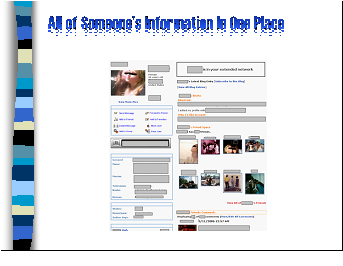
Navigation on these community websites is easy and users can move from person to person and picture to picture through hyperlinks and clicking on images. Pictures are really popular on these websites, and since parents don’t always moderate what is put up on the Internet, sometimes disgusting pictures are posted. This creates an opportunity for Internet predators – especially because a person’s site can combine pictures, blogs, profiles, and personal information all in one location. MySpace, Facebook, Blackplanet, and the other community websites try to make sure their websites are safe…but it’s not always easy for any website to do this – just like no matter where you live – there may be some places that are not that safe after dark.
Slide 42

MySpace, Facebook, Blackplanet, and all other community websites are not good or evil – they are a microcosm of what’s on the Internet. I guess no site can be correct all the time – especially if they allow any youth to have the freedom to post information about themselves. If you use MySpace, they have good information about how to protect yourself and keep yourself safe. Check it out…and discuss the safety tips with your parents.
Slide 43

Frequently, these web-communities put out surveys and questionnaires that users fill out to match up people with common interests. These questions are also sometimes posted on a user’s profile. Questions can go way beyond “what’s your favorite color,” and “who’s your favorite sports team.” But questions dealing with drugs, shoplifting, being beaten up, and physical relationships are far too common. If you answer these questions truthfully, you might disclose information you’ll later regret. What’s worse, is if you lie about something online, people will accept it as true because they can’t hear your sarcastic tone or see your silly grin. It’s so easy to lie and put things on these websites that are completely not you. It’s scary. And the sad thing is a lot of people do it. Most youth-oriented community websites have these questions that are designed to keep members on the site – but if a family decision is made that community sites are okay – use good judgment and talk to your parents about what questions you to answer.
Slide 44

We are getting to the end of our program, and now we will discuss why it’s important to be careful and responsible when posting or blogging.
Slide 45

In addition to profiles, there are also forums, chat groups, and blogs on most web communities – and on many other sites too. Many forums and chat groups are educational or reflect what teens want to talk about – but like anywhere on the Internet – (and this is not a reflection on any particular youth oriented community group) – anyone can find whatever they are looking for – or sometimes what they’re not looking for – online. Blogs, also known as web-logs, are also common nowadays, and are completely available to the public. They’re essentially a diary, online. I know that if I had a diary, I wouldn’t want to post it online. But its becoming the “norm” and it’s a huge privacy threat. Think about the kinds of personal information you want to share with the world.
Slide 46

What is really concerning is that more and more frequently, college admissions counselors, employment departments, and now school systems will check community websites to see if you have an account, and if there is anything bad in your profile. If you lie about doing something bad, it’s a strike against you. If you aren’t lying, it’s still a strike against you. In some cases students are being expelled from schools for posting threats on these websites. It’s serious, and it can effect you for the rest of your life because what you write on the Internet, never is truly erased, it ends up going into archives, and even if you try to delete a webpage, it might be indexed on a search engine or an Internet-archive site.
Slide 47

Here’s an almost day-by-day copy of what was on the MySpace website. All of the most popular websites can be searched like this. So if you write something on a community website as a joke and take it down after one day – it still may remain on the Internet forever. If you search for the term “way back machine” on any search engine – like Google – it will take you to an archive site that records what was on certain websites just like what is on this slide.
Years from now when you’re competing for a scholarship or applying for a job – write you write or blog may come back to haunt you – so write and blog responsibly.
Slide 48
There is just so much information! This just means that parents and students have to be educated and agree on what’s fair and what’s not fair to do on the Internet – because the amount of information on the Internet is almost unlimited. We recommend family discussions. Depending upon what is decided, students will know what is right and fair to do online. If a family decision is reached about parental filtering or tracking, parents can find many different products that provide filtering by conducting an Internet search or talking with someone at a store that sells software. But there is no perfect filtering or tracking solution – every family needs to talk about these issues together and decide what parameters are best for them. Knowledge is power. The more you know, the better able you are to make good decisions.
Slide 49

We’ve have talked about many of the potential dangers inherent when using the Internet this evening.
Slide 50

And now that you’ve completed this Safe Connects education program, we hope you know more about each of the topics we’ve talked about today. And thanks to the Indiana Department of Education for reviewing these slides. However, Net Literacy is responsible for all of the content.
Slide 51

Remember to have fun and stay safe! And for more information – visit www.safeconnects.org.